How to create API Key for your wordpress plugin
- nir
- July 23, 2023
- general support, Plugin
- 0 Comments
Create API Key for your WordPress plugin
In order to send push notifications to throw your WordPress site, you need to install the web2application plugin.
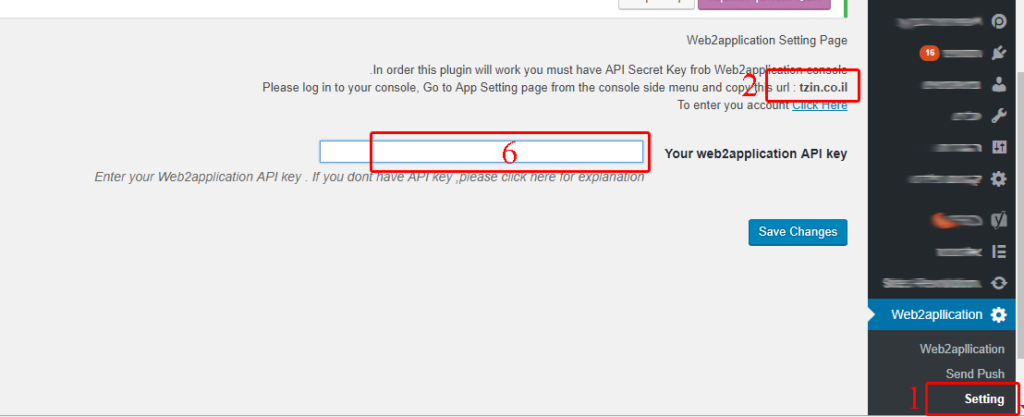
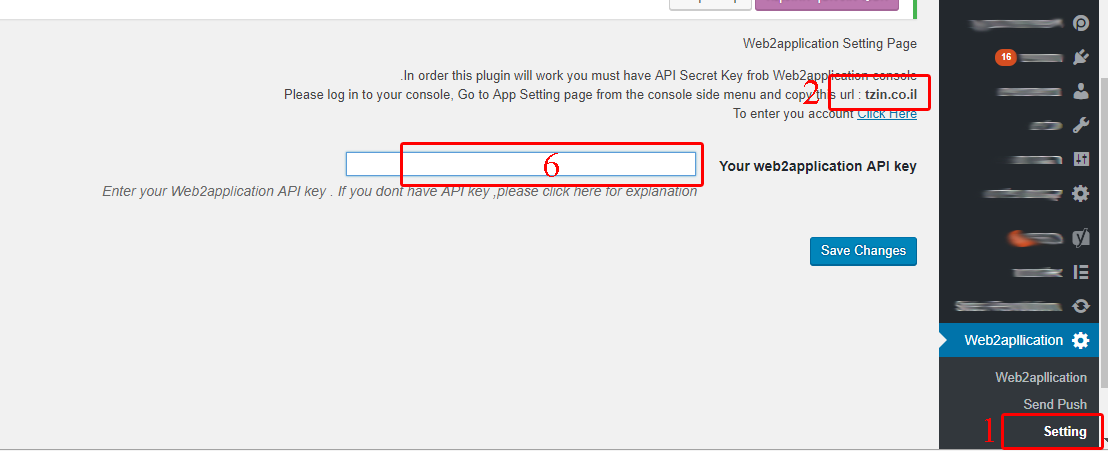
1. After installing, Go to “Setting”.
2. select and copy your URL that the plugin shows “your-domain.com”.
3. login to your web2application account and to to “Push Setting at the left menu”.
4. Paste or write your URL that the plugin gave you and click “Create API”.
5. the system will generate a special API key for your URL. Copy it and paste to the Plugin Setting ( number 6 on first image).
What Is an API Key ?
To identify and authenticate an application or user, the API key is a unique code. A white-labeled internal marketplace, for example, is a site where API keys can be purchased in bulk. They serve as a secret token for authentication, as well as a means of identifying users.
APIs (application programming interfaces) are interfaces that aid in the development of software and describe how different pieces of software work together. Requests between programs, how to create api key wordpress, and the data formats they use are all within the authority of these systems. IoT applications and websites frequently use these tools to acquire and process data or allow users to provide information. API key generators, for example, make it possible for consumers to obtain Google API keys or YouTube API keys.
User, developer, and program are all identified by an API key that is given by an application when calling an API for a website. Typically, an API key comes with a set of access rights that are specific to the API with which it is linked.
Use API Keys for a variety of reasons.
API keys are frequently employed to restrict access to and monitor the usage of an API’s interface. Preventative measures are routinely taken in order to avoid misuse or harmful use. API keys can be used for a variety of purposes, including:
Authentication API Keys for Project Sign-In
Authentication of users and the project as a whole is made possible through the usage of API keys. API keys are used to grant access to a project via:
Defintion of the Project
When performing an API call, the application or a specific project can be identified by its API key. API keys, while not as secure as tokens that allow authentication, assist identify the project or application making the call. As a result of this, they can be used to restrict access and allocate usage information to a single project..
Approval of the Project
A frequent usage of API keys is to verify that an application is authorized to make a request to the API. The API being used in the project will be enabled as part of the authorization process.
Authentication API Keys for Users
The caller requesting API access must be identified using one of several different types of authentication techniques. Authentication tokens are used by both endpoints and API servers to verify that the user has permission to make a call, and this information can be used to make a judgment on whether to approve a request.
Authentication can be done using API keys for the following:
Authentication of the User
By confirming or authenticating the user’s identity, this ensures that the person making the call is who they say they are.
Authorization by the user
When a user makes a request, this verifies that they have authorization to do so.
API Key Security
In light of the growing growth of IoT, API security is becoming increasingly crucial. A user’s sensitive personal information is transmitted between APIs and the applications and systems they interact with. A vulnerable API could therefore be a high-value target for attackers to get access to crucial data and machines and networks via an unprotected API. As a result, they must be particularly safe from attacks such as access control failures, distributed denial-of-service (DDoS), injection, and man-in-the-middle (MITM).
Using REST APIs is a standard way to secure your API, as it regulates the data that an API can access through a Uniform Resource Identifier (URI)-based Hypertext Transfer Protocol (HTTP) (URI). As a result, harmful data cannot be introduced into an API.
Related Posts
How Will Push Notifications Benefit Your Business
- nir
- July 23, 2023
Boost the performance of your business with push notifications. Push notifications allow you to ..
Master the Art of App Creation: Build Your Own Mobile Application with a Website to App Building Course
- Mike
- December 19, 2023
Welcome to the exciting world of app creation! In this digital age, where smartphones ha ..
Leave A Comment Cancel reply
You must be logged in to post a comment.